Vex
Web application vulnerability scanner that applies a technique called DAST(Dynamic Application Security Testing). It performs a simulated attack by sending a request from outside the Web server and analyzes the response to check for vulnerabilities, thus enabling efficient detection of security holes that may cause realistic threats.


Smooth File
is a file transfer and sharing service for business,
which can securely transfer/share large files that cannot be sent by email.
It enables low cost operation as it offers access by an unlimited number of users, as well as ease of use and robust security.
“PLOTT” is IT Service Vender securing communication between Companies.
With our know-how which has been fostered for fifty years as of foundation of our company, we plan, develop, offer and maintain our products which makes it secure to communicate with other in business.


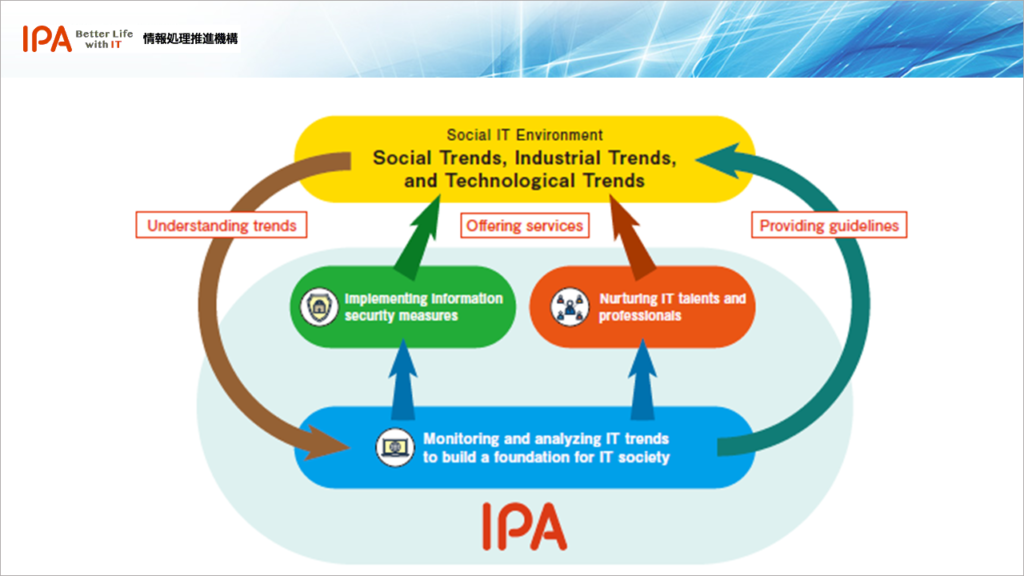
We will relentlessly monitor and analyze shifting trends in the IT society and technologies with a broad perspective. We provide guidelines and solutions for you to combat emerging social issues and to accelerate industries’growth.
We will also work aggressively to deliver more intelligent, strong IT security while developing exceptional IT talents to drive innovations. Through all these activities, we are expediting the arrival of a reliable IT society that is both safe and convenient.


SECUREMATRIX is a unique, patented, and highly secure token less matrix authentication solution, which combines patterns and images to form a one time single use password that can be used for desktops, Windows, VPNs, intranets & extranets, Web servers, e-commerce, and other network resources. It does not require a physical token yet it is as secure as a two factor security system. Our focus is on enterprise class security and authentication.

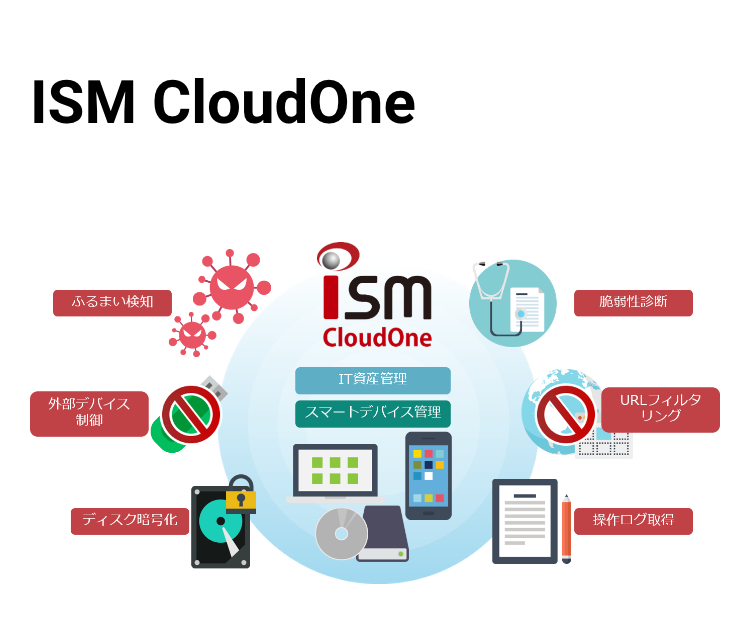
ISM CloudOne is provides a secure environment with a multitude of features anytime, anywhere, on any device
and can be used without a VPN as long as you have an internet connection.


Stena is a fraud detection AI platform that specializes in time-series data and multi-dimensional data.
Our cutting-edge detection technology is highly acclaimed in various national industries, ranging from online game user fraud detection to business expense reimbursement fraud detection.
ChillStack Inc. is a leading AI security company in Japan.
Cybersecurity Laboratory of NICT is working on R&D for cybersecurity techniques to cope with sophisticated cyberattacks and unknown and potential threats, such as ones for emerging IoT devices. We also work to automate countermeasures against cyberattacks by collecting, accumulating, and analyzing large amounts of information on diversified cyberattacks, including indiscriminate and targeted ones. Moreover, we verify the effectiveness of our research outcomes by applying them to our own cyberattack analysis, and then disseminate them to society.
You can check more about our research on NICT official website.

TRAPMAIL | GSX sends harmless training emails disguised as attack emails to the target individuals. Contained in the training emails are a URL link or an attachment file that when opened displays the relevant educational material. Additional information, such as the time of opening, is also logged on GSX’s training server. Finally, GSX compiles the training results and log data in a comprehensive report. The scope of the training is not limited to decreasing malware infections, measuring incident response capabilities, or even improving the awareness of the email recipients; the final report highlights improvements that can be made to risk control measures for the entire organization.


iDoperation is a Japanese No.1 privileged access management (PAM) software.
iDoperation streamlines and automates the process of monitoring and protecting privileged accounts.


iDoperation SC is a Japanese No.1 User Activity Monitoring software. iDoperation SC records the desktop screens of all users.
The administrator watches a video of the operation to confirm what happened.


Zero-Trust for Email
imatrix features sophisticated technologies such as high availability mail servers, high throughput anti-spam, low false positive anti-malware and accountable AI analysis system to provide a secure email communication. In order to realize safer business communication with diversified work styles, we think it is necessary not only defense against external attacks but also data leakage and internal fraud can be dealt with quickly. Moreover the products or services that realize them must protect user privacy and fairness for communication and work environment. For sustainable society, we are developing products to comprehensively support business communication, such as an AI-based outgoing email evaluation system for Zero-Trust, email message compliance management, and an authentication system for secure file transport.

IIJ SecureMX Service, No.1 Japanese market share email Security SaaS used by more than 1,400 customers in the world, is a cloud-based service that provides essential security for corporate customers. Such security features include protection against threats, erroneous transmissions, and other functionality necessary for email environments.
IIJ Secure MX Service can be used with any type of email environment, including on-premise, fully outsource email systems, cloud (Microsoft 365, Google), etc.

IIJ Global Solutions Singapore Pte.Ltd. , a subsidiary of Internet Initiative Japan Inc. (IIJ), is a specialist of Cloud and Security and providing it’s solutions in the Asia Pacific region.

Safous is a managed Zero Trust Network Access (ZTNA) service that allows pre-authorized users and/or IoT devices to securely connect to internal information resources such as business applications within the customer’s premise or in the cloud, under strong authentication, via an access point (PoP: Point of Presence) set up by IIJ. This configuration eliminates the need to allow external access to the corporate network and reduces the risk of attacks on the corporate network. The PoP can be used in eight regions (China, Singapore, Indonesia, Japan, Europe, USA, Canada, and South America), with more locations to follow.

IIJ Global Solutions Singapore Pte.Ltd. , a subsidiary of Internet Initiative Japan Inc. (IIJ), is a specialist of Cloud and Security and providing it’s solutions in the Asia Pacific region.

LanScope is an Integrated Endpoint Management tool that has been selected by more than 10,000 customers, in and out of Japan.
LanScope simplifies IT management by providing IT asset management, Insider Threat Mitigation, and Endpoint Security as a single tool.
Designed to meet the IT security and productivity management (Asset management, Log management, Web management, Device management, Threat protection, etc) needs of companies facing increasing responsibilities with limited resources.
IIJ Global Solutions Singapore Pte. Ltd. is the sole distributor in Asia Pacific region.
IIJ Global Solutions Singapore Pte.Ltd. , a subsidiary of Internet Initiative Japan Inc. (IIJ), is a specialist of Cloud and Security and providing it’s solutions in the Asia Pacific region.

Trend Micro, the global leader of cybersecurity, with vision of “making the world safe to exchange digital data”, provides full layered solution to better protect computing environment including enterprise ICT, OT/ICS and cloud platform.
Deep Discovery Inspector , a network sensor with advanced detection capability & flexible deployment option, visualizes threat in network.
ApexOne is a next generation endpoint protection suites covering both endpoint protection & endpoint detection and response.
CloudOne provides comprehensive security functions to cloud platform.
VisionOne provides full visibility to cybersecurity risk through aggregation of information / intelligences captured by security sensors.



ALog series product
ALog series product is unified log management solution. Centralized management of integrated logs enables both internal threat and external threat countermeasures. Alog can also identify suspicious behavior by using AI to detect irregularities in past logs.

Our goal is to provide security as a competitive advantage for business. Building on our product marketing ability to develop unique products, Amiya aims to raise corporate value by accelerating the pace of business through data and network security.

DataArmor
DataArmor protects your confidential information by encrypting all data, even while it is being processed – ensuring security and enabling safe sharing of the knowledge contained within.

At EAGLYS we strive to make the world a better place by creating safer and more private ways of processing and exchanging data. We do this through secure computing & processing always encrypted data.

MylogStar is security software that can acquire 15 types of operation logs, which are top class in the industry including records, manages, analyzes server access and PC operated.
ActiveImage Protector -RE is a countermeasure software of systems failure that can easily, fast backup the entire system, application, and data, save it as an image file, and easily handle all restorations including OS ,application and data.

TOSHIBA provides security products and solutions for protecting control systems in power plant and industrial infrastructure, manufactures from cyber threats and attacks.
CyberX is unified IoT/ICS(Industrial Control System) security platform to discover IoT/ICS assets, visualize device risks and vulnerabilities,
and monitor your network for threats continuously.
Waterfall Unidirectional Security Gateways enable safe IT/OT(Operation Technology) integration, disciplined control, and real-time industrial network monitoring.
CYTHEMIS™ secures and visualizes infrastructure control systems and industrial production systems in one single control platform.
Also legacy equipment without built-in security mechanisms is protected.



CSIRT (Computer Security Incident Response Team) is an organization that receives reports of security breaches, conducts investigation of the reports and responds the incidents in case of emergency.
SECWEREWOLF is a card game that can learn CSIRT’s role.
SECWEREWOLF separates players into two teams, the CSIRT Team and the Cyber Crime Team, based on the job cards they first receive. During their turns, CSIRT members can dismiss the players they believe to be cyber criminals, and the Cyber Crime Team members commit crimes during their turns (shown on their job abilities), trying to put the blame on other players to get them fired. This pattern repeats with each group trying to come out on top.



ASEAN-CBP(Cybersecurity Business Platform)